As part of a XenApp implementation I was asked to implemented two-factor authentication for the Citrix Access Gateway 5.0 VPX with SafeWord 2008.
I had configured different authentications with the Access Gateway before, but had not yet faced the combination of SafeWord and the Access Gateway 5.0 VPX, so I started with some research on the net. Even though I did find some guides for the Access Gateway 4.6 VPX implementation, it took me some time (and additional explaination from a RADIUS expert) to get all the components working together.
So here’s my blog to share the knowledge and provide an implementation guide for the configuration of two-factor authentication with SafeWord 2008 on the Citrix Access Gateway 5.0 VPX.
Required CAG VPX Licenses
Let’s start with the required licenses for the Citrix Access Gateway VPX that are required to support the two-factor authentication. As the Access Gateway is part of a XenApp implementation, it will solely be used as an ICA proxy, providing user access to published XenApp applications and/or desktops.
As can be read in this eDocs article and this knowledgebase article you only require the Platform license (which comes with the purchase of the VPX appliance) to create a Basic Logon Point that will support the required two-factor authentication (based upon RADIUS).
RADIUS
To combine SafeWord2008 with the Citrix Access Gateway VPX, you’ll need to implement a Basic Logon Point that uses RADIUS authentication. You’ll also need to install the Network Policy Server (NPS) role on your Windows 2008 R2 server to to combine it with the SafeWord 2008 components.
SafeWord2008 components
As the SafeWord components installation was performed by another team member I did not write down the entire installation process, so for now I will refer you to the provided manuals and a quick list of the installed components, which can be found on the SafeNet product Manuals site. The following SafeWord2008 components were installed on a Domain Controller (allowing for the required Schema update):
- Active Directory integration – to assign tokens to user accounts through the AD Users & Computers mmc.
- SafeWord server – Encrypted database to store configuration information.
- IAS/NAS Agent – required for RADIUS integration.
Ensure that you configure the SafeWord2008 components to work with the Windows Network Policy Server.
Configure Windows Network Policy Server (NPS)
Microsoft offers a good NPS portal on TechNet to find additional product information.
The main component for the two-factor authentication is the RADIUS server, with is configured through the NPS. As it took me some time (and help) to get all components working together, I’ll elaborate in more details on the NPS configuration. Citrix does offer a good knowledge base article CTX124420 on the configuration of the required NPS rules. You can follow the direction in this article for the configuration of the NPS, but you’ll need a different configuration on the Access Gateway than the one described in the article as we are not implementing the Access Control component for the Access Gateway.
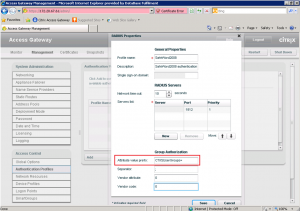
Keep track of the value entered for the Vendor specific Attribute value (Step 24 of knowledge base article CTX124420) as you’ll need to add the exact same String value in the configuration of the Access Gateway Authentication Profile. The configured string value is returned to the Access Gateway by the RADIUS server when the provided credentials are successfully authenticated.
Configure the Access Gateway
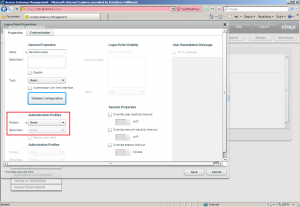
To get RADIUS and Citrix Access Gateway to work together correctly, without using additional Access Control components, you’ll need to apply the following configuration for your authentication profile:
| Screens | Actions |
|---|---|
| The most important thing for this configuration is to check the given value for the Attribute value prefix, as this needs to match the exact value entered in the NPS configuration (Step 24 of knowledgebase article CTX124420). This is the returned string from the RADIUS server the Access Gateway is accepting as a successful authentication result upon which it will continue to process the logon procedure for the logon point. | |
| To correctly configure the logon point, you’ll have to that into account that: authentication will take place at the Access Gateway, not the Web Interface, the Web Interface uses the primary authentication profile to authenticate users, configure a primary authentication profile for LDAP (check this eDocs article), use SafeWord2008 as the secondary authentication profile. |
The following sources have been used to create this post:
Access Gateway VPX Licensing for Access Gateway 5.0
CTX124138 – Citrix Access Gateway VPX and 2010 Licensing Changes FAQ
Citrix eDocs – Configuration Access Gateway VPX 5.0 Basic Settings
CTX110141 – SafeWord for Citrix Advanced Access Control Implementation
CTX124420 – How to Configure Radius Authentication/Authorization on Windows 2008 for Use on Citrix Access Gateway Standard Edition
Access Gateway 5.0 – Creating LDAP Authentication Profiles on the Appliance
Pingback: virtuEs.IT
Pingback: Kees Baggerman
Pingback: Andrew Morgan
Pingback: Louis Göhl
Pingback: Bram Wolfs
Pingback: Wout Tigelaar
Pingback: Ingmar Verheij
Pingback: RobB
Pingback: Patrick Kaak
Pingback: Jarian Gibson
Pingback: Christopher McMillan
Pingback: Arti Cijntje
Pingback: Citrix Info Group
Pingback: Sigurd Felix
Pingback: Albert Willemsen
Pingback: Wout Tigelaar